Enterprise security operations centers (SOC) have existed for the sole purpose of detecting and responding to threats to an enterprise – external or insider. In the cybersecurity realm, the protectors have never been ahead of the adversaries, and more often than not, have fallen significantly behind and have struggled to recover from cyber attacks. The challenge centers around the efficacy and relevance of detection algorithms and methodologies. Everything is dependent on detection, and yet, many enterprises almost exclusively continue to treat the symptoms – e.g., alert volume/noise, triage/response automation etc. – without addressing, yet alone solving, the core ailment: inferior detection.
For data breaches and cybersecurity threats, SOC processes haven’t changed much in a decade. Logging common data sources (e.g., raw events like domain controller logs and processed events like firewall alerts) into a SIEM (e.g., Splunk) is typically the starting point. Then come threat detection rules, typically 100’s of them, being written by threat/intel and sometimes IR analysts, on the SIEM, to produce somewhat noteworthy ‘incidents’ to investigate, followed by ad-hoc threat hunting by professionals using tools, human observation, scripts etc. to find other noteworthy ‘incidents’ the mundane rules in a SIEM may have missed or not raised as an ‘incident’.
Finally, there is incident response, a response process to investigate a fraction of the ‘incidents’ and respond appropriately, and if lucky, perhaps even add a bit of automation. From a security leader and CISO’s perspective, reporting is important, but it’s almost completely a manual collection of non-standard metrics, rarely in repeatable form, for the purposes of visually understanding the level of security preparedness of an organization.
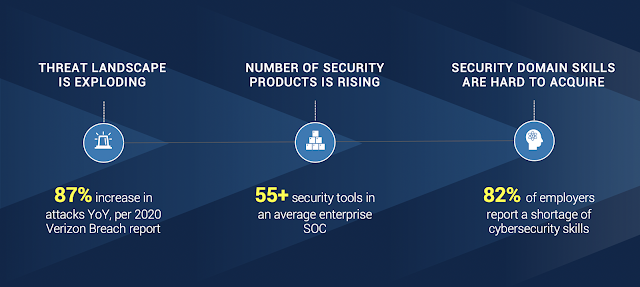
While detection tools have been seeing modest improvements, these gains are offset by fast-evolving complexity of the threat landscape, the increased volume and frequency of both new and recurring threats. According to the 2020 Verizon Breach Report, there has been an 87% increase in enterprise attacks, year over year. And this percentage has been similarly high for a number of years and does not show any signs of slowing down.
Solving the detection puzzle
One significant challenge SOC professionals face, will not, and likely cannot change: there will never be enough proactive detection or preventative content to mitigate security threats before they occur. Put more simply, there will never be a world in which the protectors are ahead of the aggressors—the best we can manage is early detection and mitigation. The average dwell time of an attack technique is a whopping 280 days before detection and mitigation, according to IBM’s Cost of a Data Breach Report, 2020.
But the bigger problem is actually a confluence of separate issues that face all security professionals. Insufficient detection capability compounded by a lack of augmentation from machine learning algorithms, not only fails to detect threats adequately, but also generates significant noise and fatigue for overworked incident responders (IR). This perfect storm of intersecting issues results in an inability to intelligently address attack patterns, utilize discrete indicators for threat hunting, and massively augment humans with machine learning.
Despite significant improvements to detection, problems still persist. Some improvements are simply incremental, while others are piecemeal solutions. The most effective detection method is building a graph across relevant and potentially indicative signals, and forming detections in the form of attack patterns, not discrete signals. This is a simple enough concept to understand yet has not been successfully implemented in most enterprise SOCs. Today it takes significant smart, deeply trained security professionals to connect these dots – a graph, if you will – and identify potential attack patterns. Such efforts have to be augmented and hence significantly expedited by machines – this is the power AI algorithms and frameworks can bring to enterprise SOCs, a force-multiplier effect.
Detection is hard
To begin with, most enterprise SOCs do not understand, in a tangible and measurable way, their state of security preparedness vis-à-vis adversary tactics and techniques; in other words, there is no comprehensive scoring that allows them to assess their own state of security preparedness from a detection defense standpoint.
The MITRE ATT&CK framework is a perfect example of such a template to measure against. This needs to be driven by data source logging, enterprise topology, enterprise priorities, current threat landscape and other relevant factors such as skills and current coverage. The next important aspect of this problem’s complexity is intelligent detection that is capable of a graph-manner of connecting the dots to detect entire patterns and making it easy to take comprehensive mitigation action, in reasonably short time-frames. Security threat analysts must be able to visualize detection scenarios for attack patterns and implement them easily, not be burdened by complex code suited to the underlying execution engine, e.g., a SIEM. Such detection scenario building doesn’t have to be done in a primary research/effort fashion – chances are someone else has solved the problem already, therefore it would be infinitely more efficient to be able to collaborate and share such solutions, at least amongst trusted partners.
Of course, in order to share any implementable code, there needs to be standardization in the code as well as unification of the underlying data models, which are hard problems to solve. Finally, incident responders need enriched alerts to eliminate painful, manual triage and investigation, which is yet another area of trial and error.
In summary, below are the main reasons why this is a hard problem to solve:
- No single metric for assessing your environment.
- Generating robust detection code to address sophisticated attack patterns is difficult.
- Threat detection tools lack the necessary standardization further aggravated by their proliferation.
- A lack of structured collaboration between peers relegates would-be partners to operate on a first-principles basis.
- Lack of unified, enriched, actionable alerts for hunting, triage & response.
A more connected experience tailored to security personnel will make the human experience less tedious and more productive.
Ideal solution for a better detection capability in the SOC
The ideal solution needs to offer:
- An automated, comprehensive and continuous assessment and scoring model that provides CISOs and SOC Managers a consistent view of their threat detection preparedness, and levers to adjust in order to improve and maintain the score.
- An AI-assisted recommendation engine that presents SOC users with relevant and personalized threat use cases they need to worry about, based on their environment, history of susceptibility and current threat landscape.
- An intelligent, preferably no-code, detection pattern-building environment that deploys highly relevant logic, and generates a low volume of high efficacy alerts for triage/response.
- A peer collaboration capability to share code, context, best practices etc. amongst teams as well as amongst enterprises, with the ability to share code that can be deployed across environments (unlike today’s inefficient and noisy IOC signal sharing through ISACs).
- A persona-friendly, visual, end-to-end, unifying experience for security professionals aimed to reduce fatigue and improve the quality and satisfaction of their daily lives.
The overall solution must give security professionals and the enterprise a consistent view of security preparedness, and the necessary implementations to keep their coverage high and their alerts rich.
Fostering collaboration amongst peers is a must in order to keep abreast, if not ahead, of the threat landscape, and allowing security domain experts to build content/logic quickly and efficiently in a no-code manner is above all key to the success of the future SOC. A collaborative, no-code approach to security threat detection will allow the experts to protect the house rather than rely on inefficient, faulty translation through developers and programming tools.
The future SOC will marry multi-product, best-of-breed, tool-agnostic threat detection with a response environment where security professionals enjoy the best support available. By developing a robust layer of relevant, custom and code-free threat detection, SOC teams can be more agile, more accurate and automate their response actions more precisely. Investment in this type of collaborative detection will help find complex and relevant attack patterns and threat scenarios, and ultimately help ensure the success of SOCs.